Keeping track of people determined to wreak havoc through computer hacks and cyber crime isn’t easy, but Microsoft officials say naming the groups is a small but important step in stopping them.
Microsoft explained its naming system for nation-state-affiliated threat entities during The National's exclusive tour of the company's cyber crime centre in Redmond, Washington.
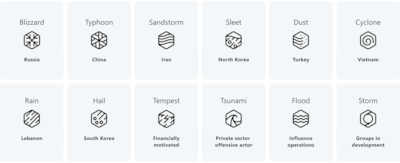
Mint Sandstorm, Storm-2035, Sefid Flood, Salt Typhoon, Cotton Sandstorm and Taizi Flood are just a few of the many names given to groups operating out of Iran, China, Russia and North Korea, which Microsoft told The National are home to some of the most active actors in the nation-state cyber crime space.
“We used to track everything as an element from the periodic table − like barium, strontium and phosphorus,” said Steven Masada, assistant general counsel of Microsoft's digital crimes unit, which leads the company's efforts to combat cyber crime around the world.
Mr Masada, who also served as assistant US attorney for the western district of Washington state, said that due to the sheer number of hacker and cyber crime groups around the world, Microsoft ran out of elements from the periodic table.
“So, we switched to the storm system, which despite some naysayers, has really caught on,” he added.
“Sleet is North Korea, Typhoon is China, Sandstorm is Iran and Blizzard is Russia,” Mr Masada continued, saying that once Microsoft researches the cyber criminals from various countries and their differing techniques, they add more details to the name, such as Mint Sandstorm, which was given to a nation-state nefarious computer cyber crime actor originating out of Iran.
For groups that aren't necessarily nation-state affiliated, Mr Masada said that other names are given.
“We use the word 'tempest' for financially motivated groups … there's one called Vanilla Tempest, which is an incredibly active ransomware group.
He added that any group with the word “flood” included in the name, is likely a disinformation or influence operation group.
Mr Masada said around the world there has been a significant increase in nation-state actor cyber crime activity. The 2024 US presidential election, coupled with the Israel-Gaza war, saw an uptick in cyber crime efforts based out of Iran.
“One example is Mint Sandstorm, it's an Iranian actor that we've taken action against … Mint Sandstorm targeted Donald Trump's campaign leading up to the most recent US election and hacked some senior advisers,” said Mr Masada.
In addition to sharing information with the hack victims and the US government, Mr Masada said Microsoft's digital crimes unit provided a criminal referral to the US Department of Justice, which later indicted three Iranians accused of the nefarious cyber activity.
The three men were allegedly employed by Iran’s Islamic Revolutionary Guard Corps, and their activities included a range of targets − including government officials, members of the media and non-governmental organisations, according to Justice Department.
Iran denied any involvement in Mint Sandstorm, yet the name, which originated from Microsoft, largely caught on.
“We do this purely to make it easy for professionals in the [cyber security] field to understand it all,” said Andrew Conway, vice president of security marketing at Microsoft.
“We associated a certain type of weather with a particular threat actor and then we made up modifiers for the types of weather,” he explained. One Russian group was given the name Midnight Blizzard.'
“We don't do this to glorify or try to make things cool, it's done for information design … we were expanding the number of threat actors that we tracked and we needed a hierarchy in which to refer to them,” said Mr Conway.
Microsoft has gone from tracking approximately 300 nefarious cyber crime groups to more than 1,500, he said.
Mr Conway said that although this naming convention seems to be catching on outside of Microsoft to some extent, not all companies, governments and organisations use the same naming system.
“There's no global standard for it,” he said.
Meanwhile, according to Microsoft, by 2028, estimates show that approximately $13 trillion could be lost to cyber crime tactics.
To blunt such cyber attacks, the Microsoft's cyber crime centre seeks to utilise security response experts from across the company to help protect, detect and respond to threats around the world.
It also uses AI to quicken the process of identifying potential threats or vulnerabilities as they come in.
Inside the cyber crime facility, there are specific offices occasionally used by the FBI, Secret Service and Department of Homeland Security to expedite investigations and collaboration efforts, depending on the cyber crime threats.
“We're increasingly seeing the blurring of lines where nation-state threat actors are becoming more sophisticated,” Mr Masada said.
“Microsoft, effectively, is a security company at this point in time,” he added, noting that besides ample technical and cyber security experts, the company also uses lawyers, investigators, data analysts and business professionals to blunt and prevent cyber crime.
According to the company, its digital crimes unit has disrupted 30 malware families, nation-state threat actors and distributors of malicious tools through civil actions resulting in the “rescue of more than 500 million victim devices”.
Our legal columnist
Name: Yousef Al Bahar
Advocate at Al Bahar & Associate Advocates and Legal Consultants, established in 1994
Education: Mr Al Bahar was born in 1979 and graduated in 2008 from the Judicial Institute. He took after his father, who was one of the first Emirati lawyers
The specs
Engine: 2-litre or 3-litre 4Motion all-wheel-drive Power: 250Nm (2-litre); 340 (3-litre) Torque: 450Nm Transmission: 8-speed automatic Starting price: From Dh212,000 On sale: Now
Company%20profile
%3Cp%3EName%3A%20Tabby%3Cbr%3EFounded%3A%20August%202019%3B%20platform%20went%20live%20in%20February%202020%3Cbr%3EFounder%2FCEO%3A%20Hosam%20Arab%2C%20co-founder%3A%20Daniil%20Barkalov%3Cbr%3EBased%3A%20Dubai%2C%20UAE%3Cbr%3ESector%3A%20Payments%3Cbr%3ESize%3A%2040-50%20employees%3Cbr%3EStage%3A%20Series%20A%3Cbr%3EInvestors%3A%20Arbor%20Ventures%2C%20Mubadala%20Capital%2C%20Wamda%20Capital%2C%20STV%2C%20Raed%20Ventures%2C%20Global%20Founders%20Capital%2C%20JIMCO%2C%20Global%20Ventures%2C%20Venture%20Souq%2C%20Outliers%20VC%2C%20MSA%20Capital%2C%20HOF%20and%20AB%20Accelerator.%3Cbr%3E%3C%2Fp%3E%0A
Huroob Ezterari
Director: Ahmed Moussa
Starring: Ahmed El Sakka, Amir Karara, Ghada Adel and Moustafa Mohammed
Three stars
COMPANY%20PROFILE
%3Cp%3E%3Cstrong%3EName%3A%3C%2Fstrong%3E%20SupplyVan%3Cbr%3E%3Cstrong%3EBased%3A%3C%2Fstrong%3E%20Dubai%2C%20UAE%3Cbr%3E%3Cstrong%3ELaunch%20year%3A%3C%2Fstrong%3E%202017%3Cbr%3E%3Cstrong%3ENumber%20of%20employees%3A%3C%2Fstrong%3E%2029%3Cbr%3E%3Cstrong%3ESector%3A%3C%2Fstrong%3E%20MRO%20and%20e-commerce%3Cbr%3E%3Cstrong%3EFunding%3A%3C%2Fstrong%3E%20Seed%3C%2Fp%3E%0A
Paris Can Wait
Dir: Eleanor Coppola
Starring: Alec Baldwin, Diane Lane, Arnaud Viard
Two stars
Who's who in Yemen conflict
Houthis: Iran-backed rebels who occupy Sanaa and run unrecognised government
Yemeni government: Exiled government in Aden led by eight-member Presidential Leadership Council
Southern Transitional Council: Faction in Yemeni government that seeks autonomy for the south
Habrish 'rebels': Tribal-backed forces feuding with STC over control of oil in government territory
UAE currency: the story behind the money in your pockets
Tips to stay safe during hot weather
- Stay hydrated: Drink plenty of fluids, especially water. Avoid alcohol and caffeine, which can increase dehydration.
- Seek cool environments: Use air conditioning, fans, or visit community spaces with climate control.
- Limit outdoor activities: Avoid strenuous activity during peak heat. If outside, seek shade and wear a wide-brimmed hat.
- Dress appropriately: Wear lightweight, loose and light-coloured clothing to facilitate heat loss.
- Check on vulnerable people: Regularly check in on elderly neighbours, young children and those with health conditions.
- Home adaptations: Use blinds or curtains to block sunlight, avoid using ovens or stoves, and ventilate living spaces during cooler hours.
- Recognise heat illness: Learn the signs of heat exhaustion and heat stroke (dizziness, confusion, rapid pulse, nausea), and seek medical attention if symptoms occur.
Sholto Byrnes on Myanmar politics
%20Ramez%20Gab%20Min%20El%20Akher
%3Cp%3E%3Cstrong%3ECreator%3A%3C%2Fstrong%3E%20Ramez%20Galal%3C%2Fp%3E%0A%3Cp%3E%3Cstrong%3EStarring%3A%3C%2Fstrong%3E%20Ramez%20Galal%3C%2Fp%3E%0A%3Cp%3E%3Cstrong%3EStreaming%20on%3A%20%3C%2Fstrong%3EMBC%20Shahid%3C%2Fp%3E%0A%3Cp%3E%3Cstrong%3ERating%3A%20%3C%2Fstrong%3E2.5%2F5%3C%2Fp%3E%0A
Ten tax points to be aware of in 2026
1. Domestic VAT refund amendments: request your refund within five years
If a business does not apply for the refund on time, they lose their credit.
2. E-invoicing in the UAE
Businesses should continue preparing for the implementation of e-invoicing in the UAE, with 2026 a preparation and transition period ahead of phased mandatory adoption.
3. More tax audits
Tax authorities are increasingly using data already available across multiple filings to identify audit risks.
4. More beneficial VAT and excise tax penalty regime
Tax disputes are expected to become more frequent and more structured, with clearer administrative objection and appeal processes. The UAE has adopted a new penalty regime for VAT and excise disputes, which now mirrors the penalty regime for corporate tax.
5. Greater emphasis on statutory audit
There is a greater need for the accuracy of financial statements. The International Financial Reporting Standards standards need to be strictly adhered to and, as a result, the quality of the audits will need to increase.
6. Further transfer pricing enforcement
Transfer pricing enforcement, which refers to the practice of establishing prices for internal transactions between related entities, is expected to broaden in scope. The UAE will shortly open the possibility to negotiate advance pricing agreements, or essentially rulings for transfer pricing purposes.
7. Limited time periods for audits
Recent amendments also introduce a default five-year limitation period for tax audits and assessments, subject to specific statutory exceptions. While the standard audit and assessment period is five years, this may be extended to up to 15 years in cases involving fraud or tax evasion.
8. Pillar 2 implementation
Many multinational groups will begin to feel the practical effect of the Domestic Minimum Top-Up Tax (DMTT), the UAE's implementation of the OECD’s global minimum tax under Pillar 2. While the rules apply for financial years starting on or after January 1, 2025, it is 2026 that marks the transition to an operational phase.
9. Reduced compliance obligations for imported goods and services
Businesses that apply the reverse-charge mechanism for VAT purposes in the UAE may benefit from reduced compliance obligations.
10. Substance and CbC reporting focus
Tax authorities are expected to continue strengthening the enforcement of economic substance and Country-by-Country (CbC) reporting frameworks. In the UAE, these regimes are increasingly being used as risk-assessment tools, providing tax authorities with a comprehensive view of multinational groups’ global footprints and enabling them to assess whether profits are aligned with real economic activity.
Contributed by Thomas Vanhee and Hend Rashwan, Aurifer
The%20specs%3A%202024%20Mercedes%20E200
%3Cp%3E%3Cstrong%3EEngine%3A%20%3C%2Fstrong%3E2.0-litre%20four-cyl%20turbo%20%2B%20mild%20hybrid%0D%3Cbr%3E%3Cstrong%3EPower%3A%20%3C%2Fstrong%3E204hp%20at%205%2C800rpm%20%2B23hp%20hybrid%20boost%0D%3Cbr%3E%3Cstrong%3ETorque%3A%20%3C%2Fstrong%3E320Nm%20at%201%2C800rpm%20%2B205Nm%20hybrid%20boost%0D%3Cbr%3E%3Cstrong%3ETransmission%3A%20%3C%2Fstrong%3E9-speed%20auto%0D%3Cbr%3E%3Cstrong%3EFuel%20consumption%3A%20%3C%2Fstrong%3E7.3L%2F100km%0D%3Cbr%3E%3Cstrong%3EOn%20sale%3A%20%3C%2Fstrong%3ENovember%2FDecember%0D%3Cbr%3E%3Cstrong%3EPrice%3A%20%3C%2Fstrong%3EFrom%20Dh205%2C000%20(estimate)%3C%2Fp%3E%0A
WITHIN%20SAND
%3Cp%3EDirector%3A%20Moe%20Alatawi%3C%2Fp%3E%0A%3Cp%3EStarring%3A%20Ra%E2%80%99ed%20Alshammari%2C%20Adwa%20Fahd%2C%20Muhand%20Alsaleh%3C%2Fp%3E%0A%3Cp%3ERating%3A%203%2F5%3C%2Fp%3E%0A
The alternatives
• Founded in 2014, Telr is a payment aggregator and gateway with an office in Silicon Oasis. It’s e-commerce entry plan costs Dh349 monthly (plus VAT). QR codes direct customers to an online payment page and merchants can generate payments through messaging apps.
• Business Bay’s Pallapay claims 40,000-plus active merchants who can invoice customers and receive payment by card. Fees range from 1.99 per cent plus Dh1 per transaction depending on payment method and location, such as online or via UAE mobile.
• Tap started in May 2013 in Kuwait, allowing Middle East businesses to bill, accept, receive and make payments online “easier, faster and smoother” via goSell and goCollect. It supports more than 10,000 merchants. Monthly fees range from US$65-100, plus card charges of 2.75-3.75 per cent and Dh1.2 per sale.
• 2checkout’s “all-in-one payment gateway and merchant account” accepts payments in 200-plus markets for 2.4-3.9 per cent, plus a Dh1.2-Dh1.8 currency conversion charge. The US provider processes online shop and mobile transactions and has 17,000-plus active digital commerce users.
• PayPal is probably the best-known online goods payment method - usually used for eBay purchases - but can be used to receive funds, providing everyone’s signed up. Costs from 2.9 per cent plus Dh1.2 per transaction.
LOVE%20AGAIN
%3Cp%3EDirector%3A%20Jim%20Strouse%3C%2Fp%3E%0A%3Cp%3EStars%3A%20Priyanka%20Chopra%20Jonas%2C%20Sam%20Heughan%2C%20Celine%20Dion%3C%2Fp%3E%0A%3Cp%3ERating%3A%202%2F5%3C%2Fp%3E%0A
Abaya trends
The utilitarian robe held dear by Arab women is undergoing a change that reveals it as an elegant and graceful garment available in a range of colours and fabrics, while retaining its traditional appeal.
COMPANY%20PROFILE%20
%3Cp%3E%3Cstrong%3ECompany%20name%3A%20%3C%2Fstrong%3EAlmouneer%3Cbr%3E%3Cstrong%3EStarted%3A%3C%2Fstrong%3E%202017%3Cbr%3E%3Cstrong%3EFounders%3A%3C%2Fstrong%3E%20Dr%20Noha%20Khater%20and%20Rania%20Kadry%3Cbr%3E%3Cstrong%3EBased%3A%20%3C%2Fstrong%3EEgypt%3Cbr%3E%3Cstrong%3ENumber%20of%20staff%3A%20%3C%2Fstrong%3E120%3Cbr%3E%3Cstrong%3EInvestment%3A%20%3C%2Fstrong%3EBootstrapped%2C%20with%20support%20from%20Insead%20and%20Egyptian%20government%2C%20seed%20round%20of%20%3Cbr%3E%243.6%20million%20led%20by%20Global%20Ventures%3Cbr%3E%3C%2Fp%3E%0A
Unresolved crisis
Russia and Ukraine have been locked in a bitter conflict since 2014, when Ukraine’s Kremlin-friendly president was ousted, Moscow annexed Crimea and then backed a separatist insurgency in the east.
Fighting between the Russia-backed rebels and Ukrainian forces has killed more than 14,000 people. In 2015, France and Germany helped broker a peace deal, known as the Minsk agreements, that ended large-scale hostilities but failed to bring a political settlement of the conflict.
The Kremlin has repeatedly accused Kiev of sabotaging the deal, and Ukrainian officials in recent weeks said that implementing it in full would hurt Ukraine.
Bookshops: A Reader's History by Jorge Carrión (translated from the Spanish by Peter Bush),
Biblioasis
THE%20STRANGERS'%20CASE
%3Cp%3E%3Cstrong%3EDirector%3C%2Fstrong%3E%3A%20Brandt%20Andersen%3Cbr%3E%3Cstrong%3EStarring%3A%20%3C%2Fstrong%3EOmar%20Sy%2C%20Jason%20Beghe%2C%20Angeliki%20Papoulia%3Cbr%3E%3Cstrong%3ERating%3A%3C%2Fstrong%3E%204%2F5%3C%2Fp%3E%0A
What are the influencer academy modules?
- Mastery of audio-visual content creation.
- Cinematography, shots and movement.
- All aspects of post-production.
- Emerging technologies and VFX with AI and CGI.
- Understanding of marketing objectives and audience engagement.
- Tourism industry knowledge.
- Professional ethics.
The Internet
Hive Mind
four stars
If you go…
Emirates launched a new daily service to Mexico City this week, flying via Barcelona from Dh3,995.
Emirati citizens are among 67 nationalities who do not require a visa to Mexico. Entry is granted on arrival for stays of up to 180 days.
Points to remember
- Debate the issue, don't attack the person
- Build the relationship and dialogue by seeking to find common ground
- Express passion for the issue but be aware of when you're losing control or when there's anger. If there is, pause and take some time out.
- Listen actively without interrupting
- Avoid assumptions, seek understanding, ask questions
Desert Warrior
Starring: Anthony Mackie, Aiysha Hart, Ben Kingsley
Director: Rupert Wyatt
Rating: 3/5
UAE squad
Humaira Tasneem (c), Chamani Senevirathne (vc), Subha Srinivasan, NIsha Ali, Udeni Kuruppuarachchi, Chaya Mughal, Roopa Nagraj, Esha Oza, Ishani Senevirathne, Heena Hotchandani, Keveesha Kumari, Judith Cleetus, Chavi Bhatt, Namita D’Souza.
French business
France has organised a delegation of leading businesses to travel to Syria. The group was led by French shipping giant CMA CGM, which struck a 30-year contract in May with the Syrian government to develop and run Latakia port. Also present were water and waste management company Suez, defence multinational Thales, and Ellipse Group, which is currently looking into rehabilitating Syrian hospitals.
Du Football Champions
The fourth season of du Football Champions was launched at Gitex on Wednesday alongside the Middle East’s first sports-tech scouting platform.“du Talents”, which enables aspiring footballers to upload their profiles and highlights reels and communicate directly with coaches, is designed to extend the reach of the programme, which has already attracted more than 21,500 players in its first three years.
Where to donate in the UAE
The Emirates Charity Portal
You can donate to several registered charities through a “donation catalogue”. The use of the donation is quite specific, such as buying a fan for a poor family in Niger for Dh130.
The General Authority of Islamic Affairs & Endowments
The site has an e-donation service accepting debit card, credit card or e-Dirham, an electronic payment tool developed by the Ministry of Finance and First Abu Dhabi Bank.
Al Noor Special Needs Centre
You can donate online or order Smiles n’ Stuff products handcrafted by Al Noor students. The centre publishes a wish list of extras needed, starting at Dh500.
Beit Al Khair Society
Beit Al Khair Society has the motto “From – and to – the UAE,” with donations going towards the neediest in the country. Its website has a list of physical donation sites, but people can also contribute money by SMS, bank transfer and through the hotline 800-22554.
Dar Al Ber Society
Dar Al Ber Society, which has charity projects in 39 countries, accept cash payments, money transfers or SMS donations. Its donation hotline is 800-79.
Dubai Cares
Dubai Cares provides several options for individuals and companies to donate, including online, through banks, at retail outlets, via phone and by purchasing Dubai Cares branded merchandise. It is currently running a campaign called Bookings 2030, which allows people to help change the future of six underprivileged children and young people.
Emirates Airline Foundation
Those who travel on Emirates have undoubtedly seen the little donation envelopes in the seat pockets. But the foundation also accepts donations online and in the form of Skywards Miles. Donated miles are used to sponsor travel for doctors, surgeons, engineers and other professionals volunteering on humanitarian missions around the world.
Emirates Red Crescent
On the Emirates Red Crescent website you can choose between 35 different purposes for your donation, such as providing food for fasters, supporting debtors and contributing to a refugee women fund. It also has a list of bank accounts for each donation type.
Gulf for Good
Gulf for Good raises funds for partner charity projects through challenges, like climbing Kilimanjaro and cycling through Thailand. This year’s projects are in partnership with Street Child Nepal, Larchfield Kids, the Foundation for African Empowerment and SOS Children's Villages. Since 2001, the organisation has raised more than $3.5 million (Dh12.8m) in support of over 50 children’s charities.
Noor Dubai Foundation
Sheikh Mohammed bin Rashid Al Maktoum launched the Noor Dubai Foundation a decade ago with the aim of eliminating all forms of preventable blindness globally. You can donate Dh50 to support mobile eye camps by texting the word “Noor” to 4565 (Etisalat) or 4849 (du).
Learn more about Qasr Al Hosn
In 2013, The National's History Project went beyond the walls to see what life was like living in Abu Dhabi's fabled fort: